Nonprofits & associations | Compliance & security
Ransomware Attack: Take Cover!
February 19, 2019
|
Ransomware, in its most basic form, is self-explanatory. Data is captured, encrypted, and held for ransom until a fee is paid. The two most common forms of ransomware delivery are through email and websites.
Just recently, one of our clients was the victim of a ransomware attack. The client lost all of their files. They had no access to their database, reports, year-end accounting — everything. Talk about a nightmare!
The only databases they have now are the ones that enSYNC holds because we uploaded them to our parent company last week. Fortunately, our team spun them up a server and gave them access to an iMIS database (which they are very grateful for as it is the only thing they have access to).
Ransomware attack
A ransomware attack is almost always initiated by clicking on something in an email that runs an executable. This delivery method could be an actual executable file or a macro in Excel. Most of the time it will appear to come from someone that you believe to be safe, which is called phishing.
What to do when you are attacked
In the case of a ransomware attack, even the most experienced computer users can panic. Therefore, every employee should know what to do if they get attacked by ransomware.
For remote staff – if you are connected to a VPN, not only could it encrypt the files on your own computer, but it could encrypt all of the files on shared drives and anyone connected to a shared drive.
For office employees – it could encrypt everything on the network.
Best practices for preventing an attack:
- Start with a good antivirus and firewall system. Keeping this security up to date is critical.
- Do not click on a link or an attachment in an email unless you can vet the source. Keep in mind, hackers and scammers can spoof trusted email addresses and domains.
- If you see something suspicious in your email, TELL OTHERS so they don't click on it.
- Keep good backups. A backup is the fastest way to regain access to your data.
- Consider using cloud services. These systems often retain previous versions of files to all you to roll back to an uninfected time.
- Keep your operating system and other software up to date because they include patches for new vulnerabilities as they are discovered.
Best practices if you have been hit:
- Don't pay the ransom because it only encourages this behavior. That's why prevention with good security software and backups is so important.
- If you do happen to open one of those fraudulent emails and click on the link, turn off the WiFi on your computer or unplug the ethernet cable to get it off the network.
- Turn off your computer as well.
- Call your IT department STAT.
If you want to evaluate your current risk level, contact us for a free evaluation of your system security.
Recent Posts
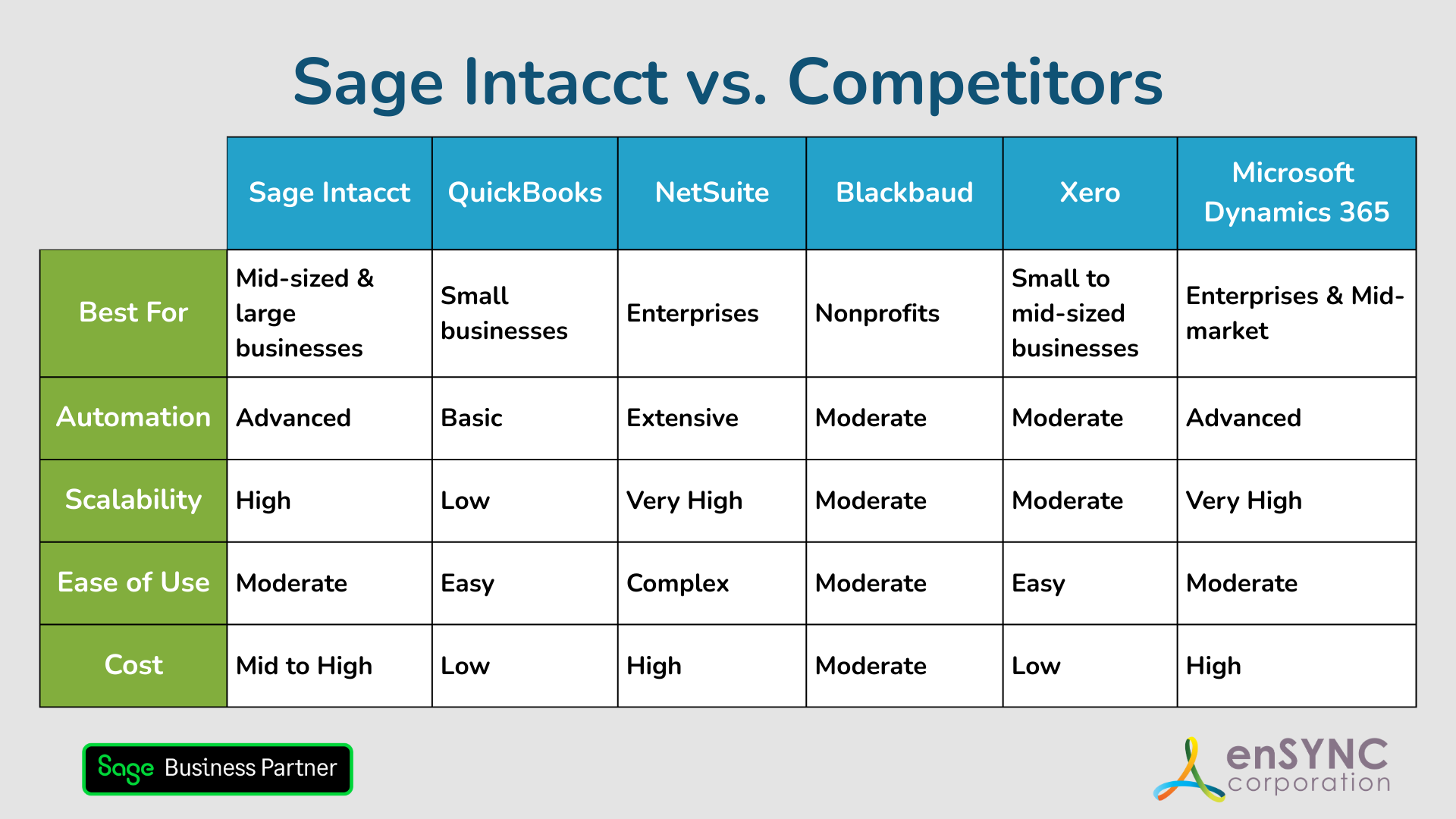
Sage Intacct vs. Competitors: Finding the Best Accounting Solution for Your Nonprofit
Choosing the right accounting software is a critical step for any organization — and a deeply personal one, too. How to choose the accounting...
How Sage Intacct Transforms Nonprofit Financial Management: A Complete Guide
Staying on top of financial management is crucial for all businesses, especially nonprofits. Nonprofits often have limited resources and handle...
Enjoying our blog?
At enSYNC, we want to empower associations and nonprofits to make well-educated decisions. If you want our industry knowledge (and other free guides) sent directly to your inbox, fill out the form below.

